Last Topic "Software Installation"
This section outlines the basic procedures for setting up the different password levels in Restaurant Manager:
Employee Passwords - allow individual employees to execute POS operations and BackOffice Functions that have been protected at a Security Level equal to or less than the Security Level of the password, itself
Master Password - gives access to ANY POS Operation or BackOffice Function protected with an Employee Password prompt.
Administrator Passwords - allows select employees to access sensitive credit card information that has been protected with a hard coded password prompt in order to meet the Data Security Standards (DSS) promulgated by the Payment Card Industry (PCI).
Daily Passwords - used by technicians who need to reset Administrator Passwords.
The Restaurant Manager Manual section on passwords outlines how and where passwords are used within the software. This section deals more with the PCI-DSS requirements of password use.
ASI Resellers, end users, and third party participants (i.e. outside network specialists) are advised to control access using unique user names and PCI DSS compliant complex passwords, to any servers/computers, and databases with payment applications and cardholder data.
The PCI DSS requires that access to all systems in the payment processing environment be protected through use of unique users and complex passwords. Unique user accounts indicate that every account used is associated with an individual user and/or process with no use of generic group accounts used by more than one user or process.
PA-DSS 3.2: Control access, via unique user name and PCI DSS-compliant complex passwords, to any PCs or servers with payment applications and to databases storing cardholder data.
PA-DSS 3.1.a: You must assign strong passwords to any default accounts (even if they won’t be used), and then disable or do not use the accounts.
Authentication credentials are not generated or managed by Restaurant Manager. Instead, authentication credentials used by the payment application are provided for by Restaurant Manager. For both the completion of the initial installation and for any subsequent changes (for example, any changes that result in user accounts reverting to default settings, any changes to existing account settings, or changes that generate new accounts or recreate existing accounts), the following 10 points must be followed per PCI 8.1, 8.2, and 8.5.8-15:
The application must assign unique IDs for user accounts. (PCI DSS 8.1)
The application must provide at least one of the following three methods to authenticate users: (PCI DSS 8.2)
a. Something you know, such as a password or passphrase
b. Something you have, such as a token device or smart card
c. Something you are, such as a biometric
The application must NOT require or use any group, shared, or generic accounts or passwords.(PCI DSS 8.5.8)
The application requires passwords to be changed at least every 90 days (PCI DSS 8.5.9)
The application requires passwords must to be at least 7 characters (PCI DSS 8.5.10)
The application requires passwords to include both numeric and alphabetic characters (PCI DSS 8.5.11)
The application keeps password history and requires that a new password is different than any of the last four passwords used. (PCI DSS 8.5.12)
The application limits repeated access attempts by locking out the user account after not more than six logon attempts. (PCI DSS 8.5.13)
The application sets the lockout duration to a minimum of 30 minutes or until an administrator enables the user ID. (PCI DSS 8.5.14)
The application requires the user to re-authenticate to re-activate the session if the application session has been idle for more than 15 minutes.
These same account and password criteria from the above 10 requirements must also be applied to any applications or databases included in payment processing to be PCI compliant. Restaurant Manager, as tested in our PA-DSS audit, meets, or exceeds these requirements for the following additional required applications or databases:
Verifone's PCCharge
Verifone's PAYWare PC
Datatran
Note: These password controls are not intended to apply to employees who only have access to one card number at a time to facilitate a single transaction. These controls are applicable for access by employees with administrative capabilities, for access to servers with cardholder data, and for access controlled by the application.
The following sections outline how you can configure Restaurant Manager to meet PCI DSS requirements
All passwords in version 19 are encrypted. In previous versions, it was possible to use DBU, or other database utility to view passwords stored in Employee.dbf and Config.dbf, these passwords are now encrypted. If DBU (or other utility) is used to change any of the passwords stored in these files, those passwords will be rendered unusable until they are reset.
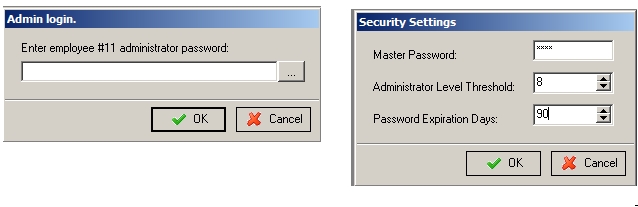
The “Master Password” in Restaurant Manager allows access to all back office as well as Point of Sale functions. It is highly recommended that the master password not be used (PA-DDS 3.1c & PCI DSS 8.5.8). By default, the Master password on a new system is 0000. When setting up a new system, you must change the Master password to something other than the default value. It is also recommended that you change the master password at least every 90 days.
Because the master password is encrypted, the program PASS0000.EXE, must not be used as in previous versions to version 15.1. After upgrading from a version prior to v15.1 and if the executable remains: it should be removed from the system. If you do execute PASS0000.EXE, or otherwise manually change or corrupt the master password on the system, it will render the master password unusable. (PA-DDS 3.2c). If this happens, you will only be able to reset the master password with assistance from ASI Tech Support. Open a help desk ticket with the subject, “Reset v19 master password”.
Restaurant Manager Version 19 relies on the concept of Administrators. They have access to settings and operations normal users do not. Those items include:
Set or Change master password, located in Setup -> Security Configuration screen. User must also be a level 9.
Set or Change other employee’s administrator password, accessible using “Edit Administrator Password Info” button in Employee Setup. User must also be equal or higher security level than the one being changed.
Modify PCI Security Configuration settings, in new Setup -> Security Configuration. User must also be a level 9.
Access the BackOffice Configuration screen.
Access sensitive credit card configuration settings in RMCCWin.
Add or Delete employees from the database.
Choosing these options in the Restaurant Manager BackOffice or RMCCWin will cause an admin password prompt to appear, or a notice that the user does not have adequate permission.
Admin passwords are set in the Restaurant Manager BackOffice under Employee Setup, click on Edit Administrator Password Info”.
NOTE: It is always the Administrator password of the LOGGED-IN user that is required. This can be confusing when an admin is trying to change the Administrator password of another Administrator. It is their own password that should be entered, not the one of the employee he is editing.
NOTE: You are allowed only six attempts to enter an administrator password. Failures to enter the correct administrator password will block additional attempts for thirty minutes (PCI DSS 8.5.13 & PCI DSS 8.5.14)
A “strong” password is an industry term to denote that the password is complex enough to reduce the chances of it being guessed using brute force methods. The rules for strong passwords are:
MUST be 7 characters or longer (PCI DSS 8.5.10)
MUST contain both letters and numbers (PCI DSS 8.5.11)
Should contain both upper and lower case letters
Should contain symbols (e.g. characters above numbers on keyboard)
Password should not be similar or contain the same numbers found in the employee password.
The last 2 are not required, but add additional password security, and make an admin password quality “excellent”.
After installing Restaurant Manager, start Restaurant Manager BackOffice (rmwin.exe) and you will be immediately prompted to create the first Administrator account, a level 9 user with access to all PCI-sensitive settings in the system. ASI recommends this account be a user tied to the reseller. It is from this user account that the reseller can continue configuring the credit card settings, and creating additional Administrator passwords for store personnel.
Resellers may wish to restrict the level 9 security level for reseller use, and have store personnel be level 8 and below. Administrators, by default, are defined as level 8 and above, configurable from within Restaurant Manager BackOffice.
Admin passwords expire in 90 days by default. After expiration, the user can no longer gain access to the admin restricted areas of Restaurant Manager. That user needs to have his password reset to regain administrator access.
EXPIRATION WARNING: The Restaurant Manager BackOffice program will warn of impending administrator password expirations upon BackOffice login. If any administrator passwords will expire within the next 10 days, or have already expired, an expiration dialog will appear listing the employees affected.
If admin passwords are forgotten, or left to expire, they will need to be reset. That can be done through the following means:
By a fellow admin- Another admin at equal or higher security level who does still have access can change the password of the user whose admin password is unusable.
By the reseller – If all store administrators have forgotten their password or let them expire, then the reseller’s own admin user can be used to reset the admin password of the highest security level store employee to allow them to regain admin access.
By calling ASI – If all admin users have lost access, the only way to regain access is to call ASI Tech Support and get the Restaurant Manager Admin Daily Passcode and follow the instructions given by the ASI technician
After retrieving the Daily Passcode:
• Re-start Rmwin and enter in the code into the password field when prompted.
• Go to “Employee- Setup”, select the employee, and click on the [Edit Administrator Password Info] button to change the admin passcode.
Password fields left inactive for a period of 15 minutes will automatically time out. You will have to begin the process again if you exceed the time frame of inactivity (PCI DSS 8.5.15).
NOTE: New passwords cannot be the same as the last 4 passwords (PCI DSS 8.5.12).
To be PCI compliant:
The default Password Expiration Days MUST be set to 90 or lower. 90 days is the default setting (PCI DSS 8.5.9).
All administrators MUST have their Expiration setting set to “System Default”. This is the default setting.
Note that Restaurant Manager allows expiration settings other than what PCI requires. This is to accommodate sites and countries that are not required to be PCI compliant (e.g. sites that do not accept credit cards). It is the responsibility of resellers, and ultimately store management to ensure that the store uses PCI compliant settings if required.
Employee Passwords consist of a four digit code that is associated with a Security Level. Every employee authorized to operate the POS System may be assigned a unique four digit code and an associated Security Level. Both are defined on the Employee Setup Form.The Employee Password, itself, is defined in the “Password” field and must consist of four digits unless the system is configured with Fingerprint Readers in which case a fingerprint may serve as the password.
Two fields on the Employee Setup Form control the Security Level associated with a particular Employee: <Clocked in Level> and Clocked out Level>. Care must be used to ensure the <Clocked in> Security Level is equal to or greater than the Security Level of all POS operations the employee is authorized to execute. While any number from zero (0) to nine (9) may be used to define the <Clocked in Level>, it is usually set to <Use Job Class> as in the screen shot below.
Linking Security Level to Job Class ensures that changing the Security Levels of certain password prompts does not also require adjusting the security level of every individual employee. For employees who work multiple jobs, the “Use Job Class” option also allows assigning different Security Levels depending on the work they’re doing.
The way Job Class Security Levels are organized, depends on the size and nature of any given business. But the chart below shows how Security Levels might be defined in a sample Table Service Restaurant. (Note that Security Level 9 is reserved for service providers):
Security Level Security Level Function Example 0-1 Line employees, bus boys Log In/Out, Print Time Slip 1-2 Basic Server Functions Starting Order, Print Guest Check 3-4 Bartender/Cashier Functions Fast Transactions, Open Cash Drawers 4-5 Shift Leader/ Assistant Manager Functions Deleting Item From Check 6-7 Manager Functions Voiding a check, Adding Menu Items, Reporting Functions 7 General Manager functions Adding Employees 8 Owners/ General Managers Managing Security Levels 9 Service Providers ONLY Configuration Settings
The only employees who may change their own Security Level are those who have a Security Level of 9 and who have been defined as Administrators. Employees are, however, able to change the Security Level and Password of Employees with a Security Level lower than their own – unless access to the Employee Setup Form, itself, is protected on the BackOffice Security Form.
Employee Passwords may be input at configurable password prompts but are never recognized at hard coded password prompts. The Master Password is recognized at any password prompt that accepts Employee Passwords.
Restaurant Manager does not allow duplicate Employee Passwords.
In Restaurant Manager version 19 all sensitive information such as passwords and credit card data are encrypted using a Triple-DES encryption algorithm. Like any other encryption algorithm, Triple-DES uses an encryption key to encrypt and decrypt the data. The encryption key is securely stored in the file KEY.DES, located in the RM working folder.
PCI security demands all default passwords and cryptographic material be removed. New installations must generate a new encryption key to comply with PA_DDS 2.7.A. This is a simple process that must be done while the session is closed and takes no more than a few minutes. From the RM BackOffice Module.
Go to Setup and click "Backoffice" on the drop down menu.
Click "Security Tab"
Click “Generate new encryption key.”
The system will automatically generate a random encryption key and update the necessary system and data files, re-encrypting all encrypted data with the new key
It is important that this file not be deleted or tampered with as it will cause all encrypted data in the system to become un-readable. You should also make sure to include this file in any system backups. Restoring a backup without this file would cause passwords and stored credit cards to be un-readable.
To ensure that credit card information is not compromised, it is mandatory that a new encryption key is generated at least once per year.
Next Topic "Security Key (Dongle) Installation"